
Microsoft has already released emergency updates to patch the Meltdown and Spectre bugs. However, considering the complexity of the bugs and due to some anti-virus software, your Windows system may or may not be fully patched. Though the regular Windows update screen won’t give you any details about the patch level, Microsoft published a simple PowerShell script that lets you know if your Windows system is fully patched or not. The following instructions show how to use it to check your system.
Update Windows
Before checking your system, I would recommend you check and update Windows. To update Windows, open the Settings app by pressing the keyboard shortcut Win + I and select “Update and Security.”
Now, click on the button “Check for Updates” and install any available updates. Once you are done with that, you can proceed and check if your system is fully patched.
Check If Your System Is Patched
Microsoft issued a simple PowerShell script that will tell you if your system is patched against Meltdown and Spectre. All you have to do is download and execute the script within PowerShell. Do note that the following procedure is applicable to Windows 7 and 8, too.
Like many things in Windows, you need to have admin rights to execute the script. Search for PowerShell in the Start menu, right-click on it and select the option “Run as Administrator.”
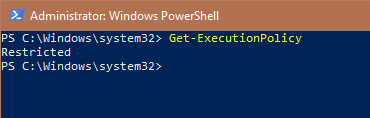
Now, even though you have administrative privileges, PowerShell won’t let you execute downloaded scripts directly. This is because PowerShell is in a restricted mode by default. You can use the below command to check your current execution policy.
Get-ExecutionPolicy
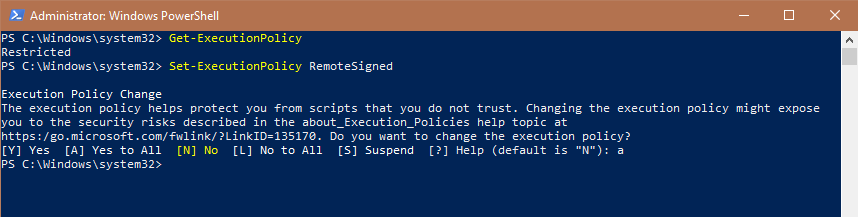
To download and execute the script, we need to change the execution policy. To do that, execute the following command:
Set-ExecutionPolicy RemoteSigned
When prompted, type A and press Enter to confirm the change. It will change the Execution policy to “RemoteSigned.” Don’t worry, you can revert it back to its original version later.
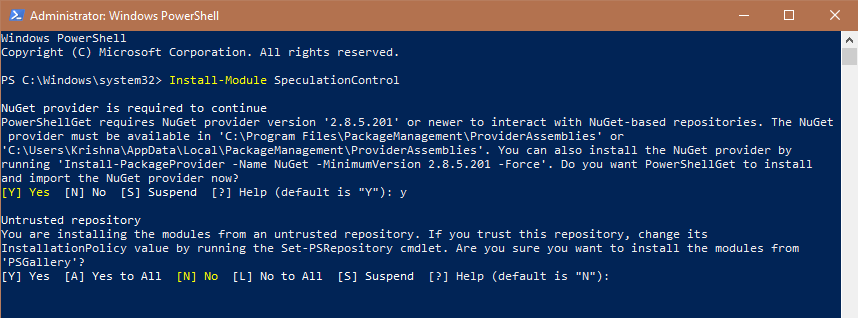
After changing the policy, execute the below command to download and install the verification script:
Install-Module SpeculationControl
While installing, if you are prompted to update NuGet, type Y to continue. You might also receive an untrusted repository warning. You can ignore the message and type A and press Enter to install the script.
Note: For those who are receiving command not recognized error, you can download the “Speculation Control Validation PowerShell Script” and extract it to a folder on your desktop. Open the folder, press Shift + right-click in it and select “Open PowerShell here.”
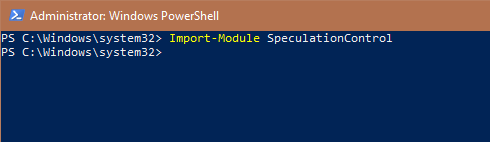
After installing, import the script using the below command:
Import-Module SpeculationControl
Once the script has been successfully installed and imported into PowerShell, you can use it check your system. Just execute the below command:
Get-SpeculationControlSettings
As soon as you execute the command, the script will scan your system and give you an output similar to the following image.
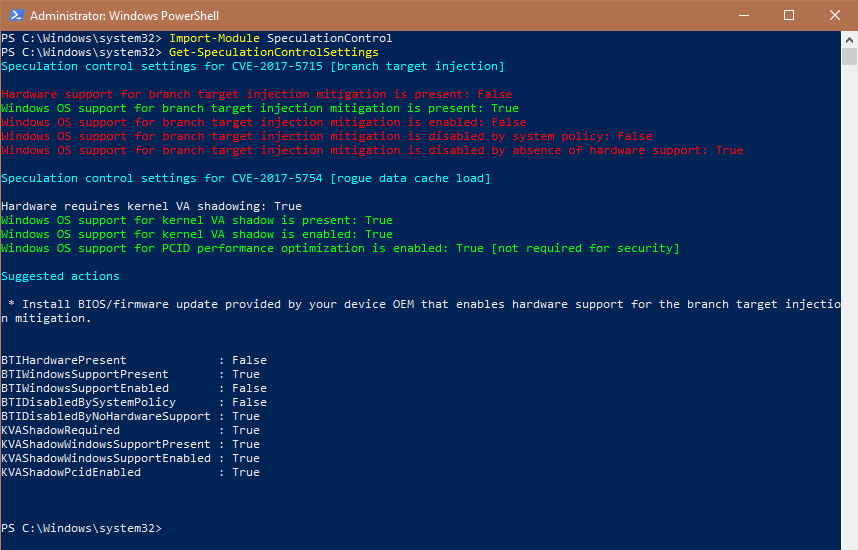
If you are seeing the same result as in the above image, it means you are protected against the Meltdown bug but received an incomplete patch for the Spectre bug.
This is because, due to how processors work, the bug is hard to patch. As such, the OS level patch requires an update to your chipset firmware. You can usually download the said update directly from the official website of your system manufacturer.
Once you’ve updated the chipset firmware, Windows will automatically install the complete patch. When your system is completely patched, you will see all green and no red in the PowerShell window.
That being said, depending on your system’s age and manufacturer, you may or may not receive the chipset firmware update. However, the Spectre bug is also hard to exploit. Moreover, most of the user applications like Chrome, Firefox, Edge, Internet Explorer, etc., are being updated to mitigate the attack as much as possible.
Because of this, don’t forget to update all your applications along with your Windows system for better security.
Once you are done with everything, you can use the below command to change execution policy back to being restricted:
Set-ExecutionPolicy Restricted
You can don’t have to change the execution policy back to “RemoteSigned” if you just want to check if your system is fully patched. You only need that when you are installing a third-party PowerShell script.
Image credit: Binary code
Vamsi is a tech and WordPress geek who enjoys writing how-to guides and messing with his computer and software in general. When not writing for MTE, he writes for he shares tips, tricks, and lifehacks on his own blog Stugon.
Subscribe to our newsletter!
Our latest tutorials delivered straight to your inbox
Sign up for all newsletters.
By signing up, you agree to our Privacy Policy and European users agree to the data transfer policy. We will not share your data and you can unsubscribe at any time. Subscribe
