Recently, a new piece of malware has been wreaking havoc online, locking innocent users out of their files and demanding money. Cryptolocker is a form of virus known as “ransomware” – a variety that attempts to extort money in exchange for providing users with what they already own, but can no longer access.
So what is it about Cryptolocker that changes the game, and how do you prevent yourself from falling victim to this vile threat. That is precisely what we want to look at today.
What Exactly is Cryptolocker?
It’s a simple question, and the answer is “malware”, but things go deeper than that because all of this is far from being simple. To get a deeper look, we will see what the security experts have to say.
Brian Krebs, who previously covered security for the Washington Post, and currently runs the Krebs on Security blog, states
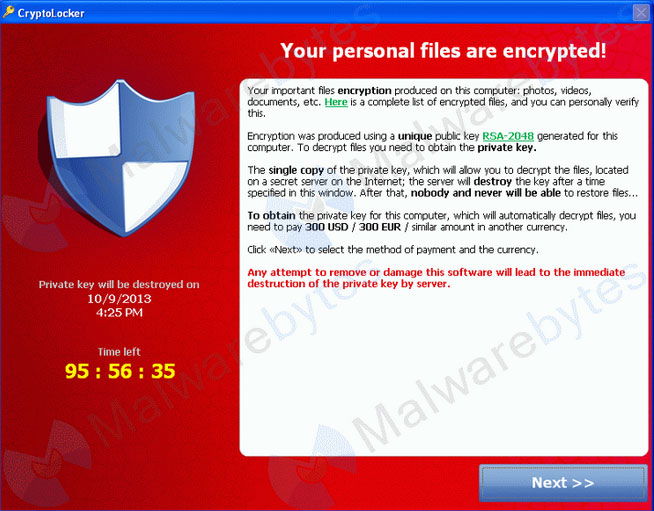
Cryptolocker is a diabolical new twist on an old scam. The malware encrypts all of the most important files on a victim PC – pictures, movie and music files, documents, etc. – as well as any files on attached or networked storage media.
Krebs goes on to explain:
Cryptolocker then demands payment via Bitcoin or MoneyPak and installs a countdown clock on the victim’s desktop that ticks backwards from 72 hours. Victims who pay the ransom receive a key that unlocks their encrypted files; those who let the timer expire before paying risk losing access to their files forever.
In recent days, the thieves have begun allowing victims more time to pay – an obvious effort to simply collect more money. After all, those traveling may still pay once they return and discover the problem.
Security expert Steve Gibson explain that
it installs itself into the Documents and Settings folder under a randomly generated name and adds itself to – and this is Windows only – to the Windows autorun list so that it executes every time you run Windows or start up Windows. It produces a lengthy list of random-looking server names in the domains of .biz, .co.uk, .com, .info, .net, .org, and .ru.
How Do You Get it?
It is typically installed through phishing attacks in email. So people will get an email that looks reasonable to them, and they will click on a link, and it’ll be an executable, and they will now be infected. Don’t be fooled by files that appear to be something else – a Word document or PDF, for instance, as these can still be stealth EXE files.
However, more recent research has shown the problem branching out – the malware also can now be deployed by hacked and malicious web sites by exploiting outdated browser plugins.
Avoiding it
The simple answer is to not open email attachments unless you are positive they were sent by that person and they are files you anticipated receiving. If you’re in doubt then contact the sender and inquire. Check the file properties also – malware.pdf may in fact be “malware.pdf.exe”.
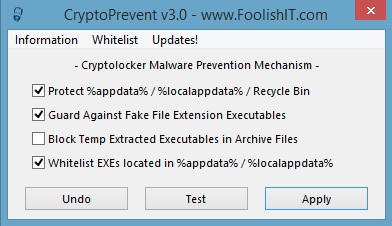
A new utility released by Foolish IT (yes the name is silly, but the company is not) can also help out. CryptoPrevent “is a tiny utility to lock down any Windows OS (XP, Vista, 7, 8, and 8.1) to prevent infection by the Cryptolocker malware or “ransomware”, which encrypts personal files and then offers decryption for a paid ransom”.
Conclusion
While CryptoPrevent can help, the best defense for users is always the same. Its all about behavior. Don’t do stupid things and don’t visit potentially dangerous web sites. In other words, always err on the side of caution. This threat shows little sign of abating and antivirus does next to nothing to prevent it from striking. It really is a jungle out there.
Alan is an avid fan of all things technology, including Microsoft, Android, Google, and more. When not writing about or using gadgets and software, he can be found on the trails hiking or mountain biking.
Subscribe to our newsletter!
Our latest tutorials delivered straight to your inbox
Sign up for all newsletters.
By signing up, you agree to our Privacy Policy and European users agree to the data transfer policy. We will not share your data and you can unsubscribe at any time. Subscribe
